2020 Election Security Procedures Violated – Why The County Will Not Provide Routers, Splunk Logs, Fobs – INDICT THE SUPERVISORS!
Maricopa County still has not provided answers or complied with the Arizona Senate subpoenas after the earth-shattering hearing last Wednesday.
One of the major concerns presented by audit officials surrounded the administrative account passwords and the missing event logs that were deleted by 37,646 consecutive login queries in one day.
Every election Administrator account, no matter the user, all have the same password.
The system only has 8 users which shows that somebody ran a script with over 37,000 queries and deleted the election security logs prior to February 5th.
We don’t know where the script came from because Maricopa County refuses to comply with Arizona Senate subpoenas.
The Senate needs routers, splunk logs, and iButton fobs to see how the systems were configured, if they were connected or modemed, and who did what.
If all passwords are the same, anybody who knows the password can sign into any account, therefore we can’t even trace actions to a specific user.
These passwords also have not been changed since Dominion software was installed in 2019. We don’t know who else had access to these machines.
This was a direct violation of the Arizona Secretary of State Election Procedures Manual that says.
passwords must: be changed on a regular basis and may not be a vendor-supplied password
The manual also states that systems may not be connected to the internet, communications devices, or any external network (except for e-pollbooks).
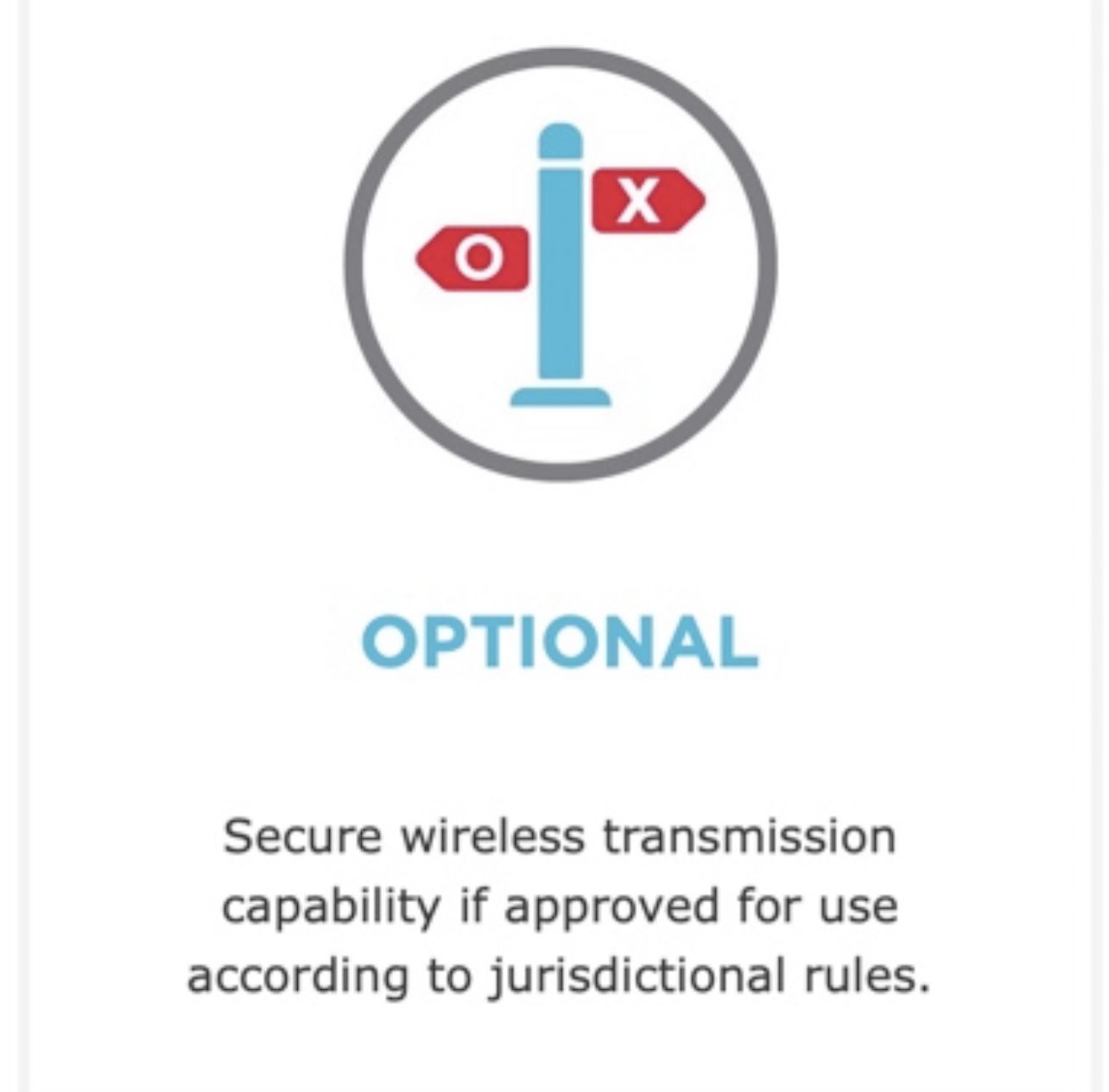
Dominion ICP Features
The image above, from the description of Dominion ICP Machines, shows that they have wireless network capabilities. Why do we use systems that can connect to the internet?
E-pollbooks and Ballot on-demand printers are allowed connection to the machines along with network connectivity according to the elections procedures manual.

Page 98: Arizona Secretary of State Elections Procedures Manual
They must use best practices for information and network security, which would include changing passwords regularly and different passwords for each username. They did not do these things.
We do not know if they were connected to secure networks because the county refuses to provide routers and Splunk logs.
Since installation in August 2019, there have been no antivirus updates, no operating system updates, or any security patches on the machines.
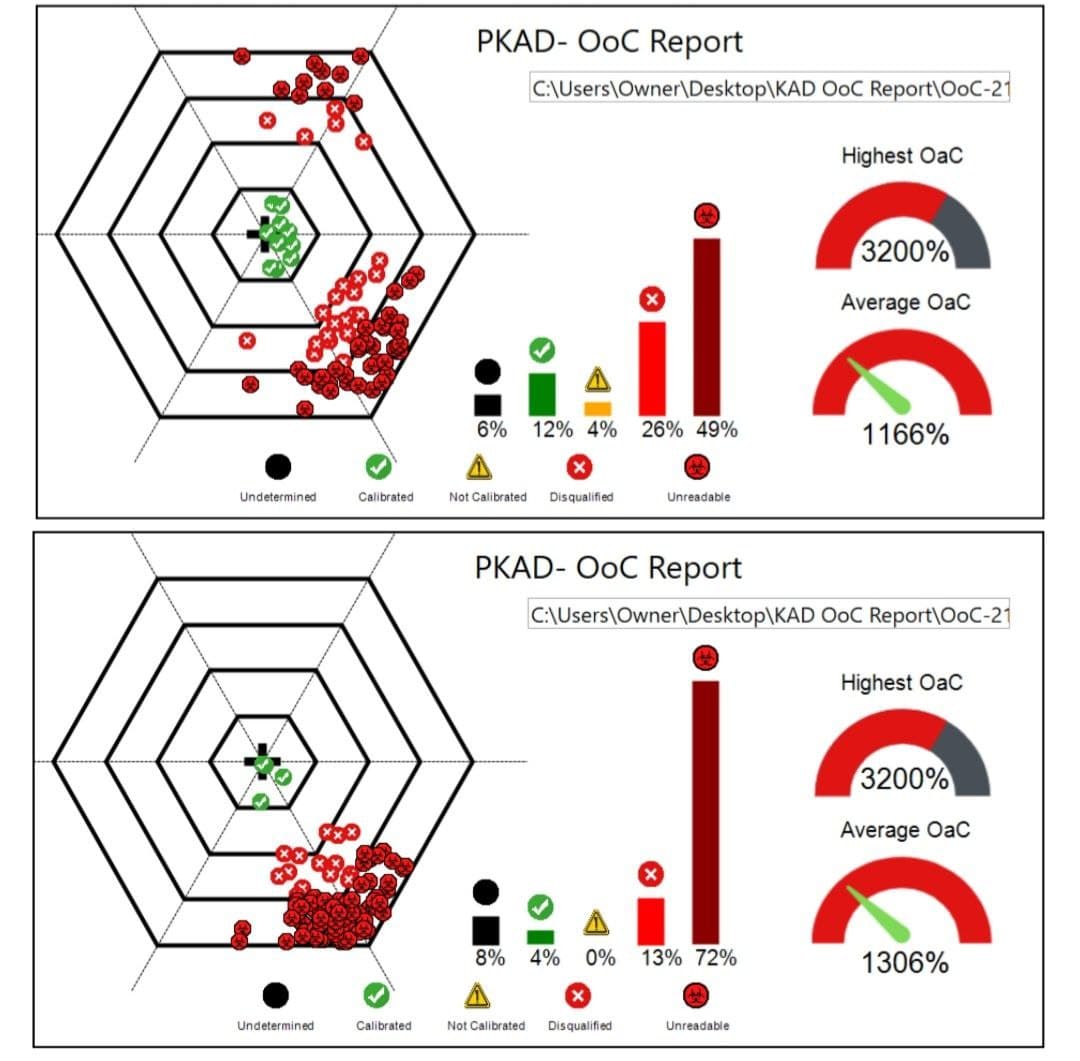
Does this explain why on-demand ballots were misprinted with offsets of up to 3200%? Did somebody hack and change the system configuration of on-demand printers?
In addition, Maricopa County’s Twitter account says, somebody “was “inappropriately accessing and downloading”, in other words breaching, “publicly available information”.
A Maricopa County Employee described this information breach as an “intrusion” and scrubbing of voter registration information. This is the same “publicly available” information that the county referred to. Police “raided the individual’s home” and retrieved this data within seven hours.
They raided his home and arrested him for inappropriately accessing publicly available info?
Were the E-pollbooks, which are connected to tabulators and WiFi accessed?
We cannot know without the subpoenaed routers, passwords, Splunk logs, and iButton fobs.
The routers show when and where data was transmitted to and from. Splunk logs log this data along with the MAC address of the device which was utilized.
What will this data show us? Did any tabulation machines’ MAC addresses ever touch the internet?
Why is the county still refusing to comply with the investigation of these election law violations?
They say that they did their own audit, which looked at none of these critical security concerns.
They also claim to not have access to these items.
If true, Dominion has complete and total control over the election and Maricopa cannot independently verify the system configuration is good.
The elections procedures manual was violated.
What else is the County hiding?
The supervisors need to be jailed! Weak RINO Paul Boyer failed his constituents when he killed the previous resolution to do so.
Who ran a script with over 37,000 login queries and deleted data prior to February 5th?
